ChromeDumper - Revealing Hidden Treasures
Introduction
I am happy to introduce my new tool, ChromeDumper. It is a tool designed to extract and analyze critical data from Google Chrome’s internal databases. As a powerful utility, it overcomes the encryption challenges posed by Chrome’s security measures, allowing users to delve deep into the browsing history and unearth valuable insights. In this blog post, we’ll explore how ChromeDumper enables red teamers, penetration testers, and security professionals to access and interpret data that might otherwise remain hidden.
Before we begin with ChromeDumper’s capabilities, let’s take a look at Google Chrome’s default browsing history. As you might expect, it’s neatly organized and accessible to the user through the browser’s interface. However, this is just the tip of the iceberg. Much more data is stored beneath the surface, awaiting extraction with the right tools.
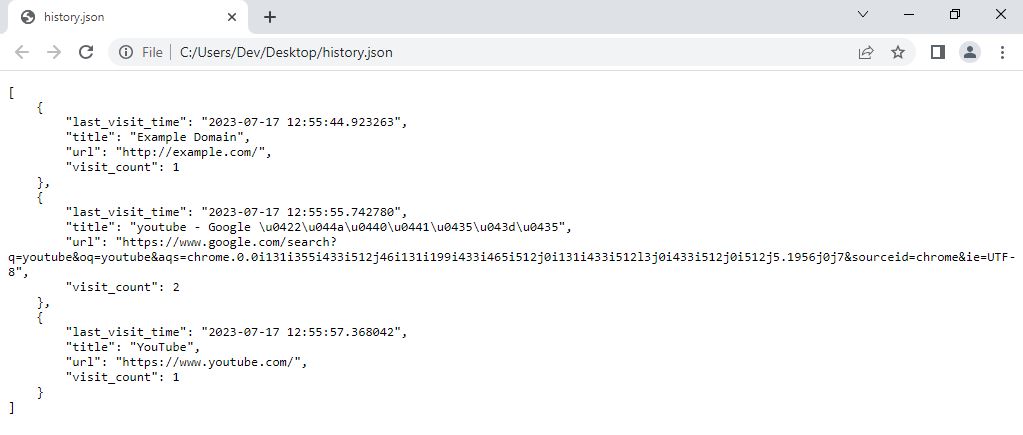
Here’s where ChromeDumper takes center stage. Using its sophisticated decryption techniques, the tool gains access to Chrome’s internal databases and retrieves a comprehensive browsing history that includes hidden URLs, timestamps, and other essential details. This deeper level of data provides an invaluable advantage for security assessments and investigations.
ChromeDumper doesn’t stop at just extracting data; it goes the extra mile by offering options to save the retrieved information. Users can export the extracted data to either JSON or CSV files, providing a structured and easily readable format for further analysis. This feature streamlines the process of sharing and presenting findings during security assessments, making it a valuable asset for any security professional’s toolkit.
As a red teamer or penetration tester, you know the value of information in simulating real-world attacks and identifying potential vulnerabilities. ChromeDumper arms you with the ability to examine the browsing habits, login credentials, and session data stored in Chrome’s databases. This newfound knowledge can be leveraged to evaluate security defenses, reveal potential attack vectors, and devise effective strategies for safeguarding sensitive information.
Chrome’s Security Measures
Google Chrome employs several security measures to safeguard user data, including encryption of sensitive information like passwords and cookies. These security measures make it challenging to access and extract data without the appropriate encryption keys and decryption methods. ChromeDumper utilizes the decryption techniques specific to Chrome’s implementation to overcome these security measures.
Additionally, you can refer to the official Google Chrome documentation on “How Chrome protects your passwords and data” to gain a deeper understanding of Chrome’s security features related to password protection. This documentation provides valuable insights into the measures taken by Chrome to safeguard user passwords and can be a valuable resource for understanding Chrome’s data protection techniques.
Unveiling Chrome Secrets Internals
To truly appreciate the power and significance of ChromeDumper, it’s essential to understand how Google Chrome works internally and the challenges it poses when it comes to extracting its data. Google Chrome stores a vast amount of user data to enhance the browsing experience and provide personalized features, including passwords, browsing history, downloaded files, cookies, and more. This data is organized in various internal databases, typically stored in the user’s profile directory. Chrome employs strong encryption techniques to safeguard sensitive user data, encrypting passwords and certain cookie values to protect them from unauthorized access. While this adds security, it also poses a challenge for extracting and interpreting the data.
One of the key techniques employed in data decryption is the combination of CryptUnprotectData and AES encryption. CryptUnprotectData is a function provided by the Data Protection API (DPAPI) in Windows, commonly used to decrypt sensitive data such as passwords by leveraging the user’s credentials and environment. In the code of ChromeDumper, the encrypted key from the Chrome profile is passed to CryptUnprotectData, which uses the user’s credentials to decrypt the data. The decrypted key is then utilized as the encryption key for the AES cipher, an advanced symmetric encryption algorithm widely used in data security. In this case, AES operates in GCM (Galois/Counter Mode) for authenticated encryption.
However, it's important to note that this decryption technique is tied to the user's credentials and the specific computer where the data was encrypted. When running the tool on the victim machine to access Chrome's internal databases, appropriate permissions are not required. Nevertheless, reproducing this technique on another computer may not work as the encrypted key is unique to the user's credentials and environment.
ChromeDumper overcomes these complexities by leveraging advanced techniques and APIs. The tool successfully retrieves and decrypts the desired information, providing users with a simplified and efficient way to access Chrome’s valuable data.
Example of how ChromeDumper interacts with Chrome’s internal databases, handles encryption, and retrieves meaningful data, empowering users to extract and utilize Chrome’s secrets.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
def get_encryption_key(chrome_profile_dir):
local_state_path = os.path.join(chrome_profile_dir, 'Local State')
with open(local_state_path, 'r', encoding='utf-8') as f:
local_state = json.load(f)
encrypted_key = base64.b64decode(local_state['os_crypt']['encrypted_key'])
decrypted_key = win32crypt.CryptUnprotectData(encrypted_key[5:], None, None, None, 0)[1]
return decrypted_key
def decrypt_data(data, key):
iv, encrypted_data = data[3:15], data[15:]
cipher = AES.new(key, AES.MODE_GCM, iv)
decrypted_data = cipher.decrypt(encrypted_data)[:-16].decode()
return decrypted_data
In this example code, the get_encryption_key function retrieves the encrypted key from the Chrome profile’s ‘Local State’ file. It uses CryptUnprotectData to decrypt the key by leveraging the user’s credentials and environment. The decrypted key is then passed to the decrypt_data function, which takes encrypted data and the decryption key as input. The function uses AES encryption with GCM mode to decrypt the data and returns the decrypted result.
Note, if you want to dive deeper into the details of CryptUnprotectData, you can explore the official Microsoft documentation at: CryptUnprotectData - Microsoft Documentation.
Limitations of the Tool
Like any other tool, has certain limitations and considerations that should be taken into account. Here are some key points to consider:
To execute ChromeDumper and access Chrome’s internal databases, Python needs to be installed on the victim machine. However, no elevated privileges are required. Depending on the operating system and user account settings, the tool can be run with regular user permissions.
ChromeDumper needs to be executed on the victim machine where Google Chrome is installed. This is because the tool interacts directly with Chrome’s internal databases and encryption mechanisms. Simply copying the Chrome database files to another machine will not provide access to the encrypted data.
Future Optimization and Native Implementations
To address the concern of Python dependency and make the tool more accessible on Windows machines, it is possible to consider developing native implementations of ChromeDumper using languages like PowerShell or C#. These native versions can provide the same functionality while eliminating the need for Python installation.
A PowerShell version of ChromeDumper would leverage the scripting capabilities of PowerShell, making it native to Windows and readily available on most machines. The tool’s logic and functionality can be ported to PowerShell, allowing users to execute it directly without additional dependencies.
Developing a native Windows application using C# would provide a robust and user-friendly interface for ChromeDumper. This would involve rewriting the tool’s functionality in C#, taking advantage of libraries and frameworks available in the
.NET. The resulting application would not require Python installation and can be easily distributed as an executable file.
By exploring these options for future optimization, ChromeDumper can become more accessible, especially for red teamers and pen testers, who won’t need to install Python on the victim machine. Providing native implementations in PowerShell or C# ensures broader compatibility and simplifies the execution process, making it easier for these professionals to extract and analyze data from Google Chrome on Windows systems without the additional requirement of Python installation. These native versions would allow red teamers and pen testers to effortlessly utilize ChromeDumper as part of their security assessments and investigations, streamlining the data extraction process and enhancing their ability to gather valuable information from Chrome’s internal databases. The tool’s enhanced accessibility and user-friendly interface can significantly aid in assessing system vulnerabilities and improving overall security practices.
Conclusion
ChromeDumper emerges as a powerful tool for red teamers, penetration testers, and security professionals seeking to uncover the valuable data from Google Chrome’s internal databases. With its decryption techniques, this tool unlocks valuable data, including browsing history, passwords, cookies, and downloaded files, empowering security assessments and investigations.
You can find the ChromeDumper tool, on GitHub. The tool is publicly available and hosted on my GitHub repository ChromeDumper. It is an open-source project, allowing users and developers to access, review, and contribute to the codebase. By visiting the repository, you can explore the tool’s functionalities, access the source code, and find instructions on how to use it effectively for red team engagements. Feel free to fork the repository, submit issues, or contribute enhancements to further improve the tool’s capabilities and utility in the realm of cybersecurity. Happy red teaming!
References
I would like to express my gratitude to the following blogs for providing me with the inspiration to create my tool, “ChromeDumper”:
Thanks for sharing your knowledge and resources, which greatly contributed to the creation and success of “ChromeDumper.”
The article was written by M4rt1n3zz